2024
Pentesting in Action
In this capture the flag (CTF) exercise, courtesy of TryHackMe, I demonstrate my knowledge and proficiency with using tool to enumerate hidden directories to get initial access to a vulnerable machine, and then take advantage of privilege escalation vulnerabilities to gain root access. The exercise requires use of the following pentesting elements: I begin by […]
Wireshark: Malware Analysis
RedLine Stealer is one of the most prolific and common info stealer logs. It is typically distributed through phishing emails, malicious websites, or in software. Once installed on the system, RedLine can harvest a wide range of sensitive information, including passwords, credit card information, crypto wallet seed phrases, cookies, app data, etc. It can also […]
Python: ARP Spoofing Program
With this Python project, I will build off of my previous coding project of creating a network scanner. With the ability to scan a network to discover users, I can now build an ARP spoofing program which will allow me setup a MITM (man-in-the-middle) attack. MITM can easily be achieved by intercepting ARP requests/responses between […]
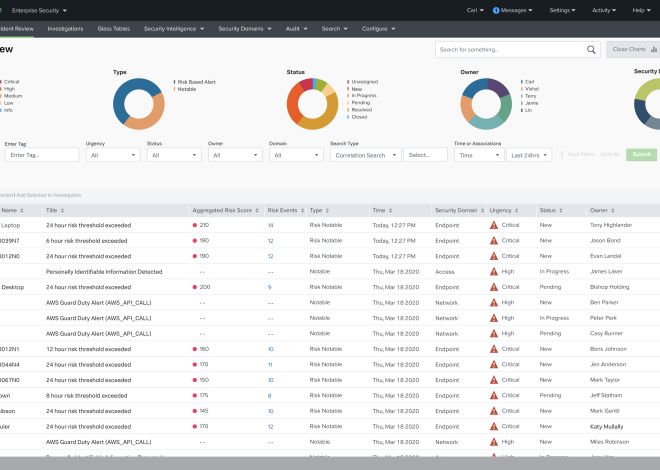
Splunk: SOC Analysis of Windows Events Logs
Welcome to my walkthrough of this Splunk room “Benign” on TryHackMe, an engaging and instructive simulation to showcase my proficiency with using Splunk to discover a suspicious executable that is masquerading as a harmless application. I will explain the steps I take to unpack and analyze the incident using the tools and techniques that are […]
Python Script: Network Scanner
Using Python, I demonstrate my ability to create a network scanner for discovering users. This allows me to discover all clients on the network and display the IP and MAC address for each. I will then be able to use this information for a red team exercise on network penetration in a separate post. Many […]
Linux Persistence Techniques
Linux persistence techniques are methods used by attackers to maintain access to a compromised Linux system across reboots, updates, or attempts to remove the malware. These techniques are crucial for cyber attackers to ensure that their malicious foothold on a system remains undetected for as long as possible. Some common Linux persistence techniques include the […]